Let’s be honest. Reports of big businesses losing data – and cash - to devious IT nerds due to various reasons but mostly because of a lack of a cyber security solution don't raise your eyebrows to the heights they once did, do they?... ZZZzzz…
Didn’t think so.
The big cyber-crime stats have lost their impact. You’re used to hearing them and after all you’re “just a small or medium business”, so it’s “unlikely to happen“ to you, right?
Plus, you can “make do” because you’re “too small and not big enough to matter”, right?
So, instead of raising the question “what are you doing to protect your business?” let’s change it and keep it closer to home.
What would you do with $488,692.27?
Grow and scale your revenue? Invest in your business? Settle your business debt? Make payroll? Reward your team?
Why $488,692.27?
Because that’s the combined amount of cash we’ve witnessed local small and medium businesses lose to cyber-crime. Not multi-million-dollar empires. But local West Australian businesses. For some, that’s the difference between running a business and having a business to run, at all.
How does it happen?
Your team.
That comes off a little strong, so let me explain. The margin of error in the world of cyber security is small. Really small. It’s often the difference between clicking:
or

While your team members might be the unexpected villains of this story, they’re not entirely at fault. And that’s because cyber attackers use a combination of:
- crafty tech skills to exploit traditional (AKA: out-of-date) security measures,
- malicious software applications, and
- sophisticated deception methods to manipulate your team members into divulging confidential information without realising it (AKA: Social Engineering).
But before you say, “Pfft! Our systems aren’t out of date - I'll have you know that my anti-virus is updated regularly!”. Be aware that with the likes of:
- zero-day vulnerabilities,
- man in the middle attacks, and
- sophisticated phishing emails,
there’s more to fighting off cyber-attacks than updating your anti-virus and ticking the ‘we’re secure’ box in your annual risk report. Especially when it comes to that last one. Phishing. And for most small and medium businesses, almost all cyber-attacks start with phishing.
Devious IT geeks got sophisticated
Personally, I miss receiving emails with badly composed sentences and spelling mistakes promising that I’ll reimburse $10,000+ by a prince stranded at the international space station.
Not only were they amusing, but they also stood out as an unnecessary IT expense on your end-of-year reports, which made them easy to spot and mitigate.
Today, cyber attackers don’t need to create elaborate stories and imitate fictional characters to lure you into an ill-judged tap of the thumb. They’ll just create perfect imitations of your emails instead.
Take a look.
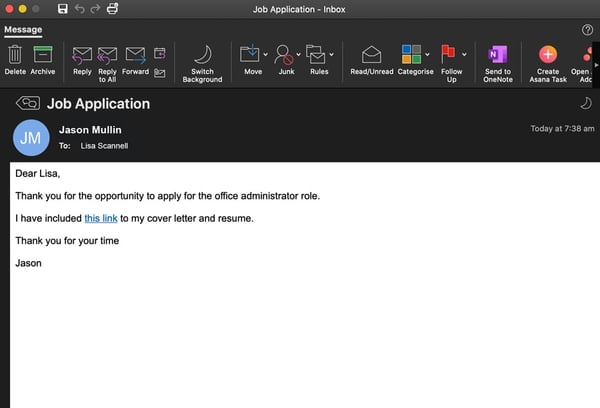
Phishing email example - Job application to an HR manager
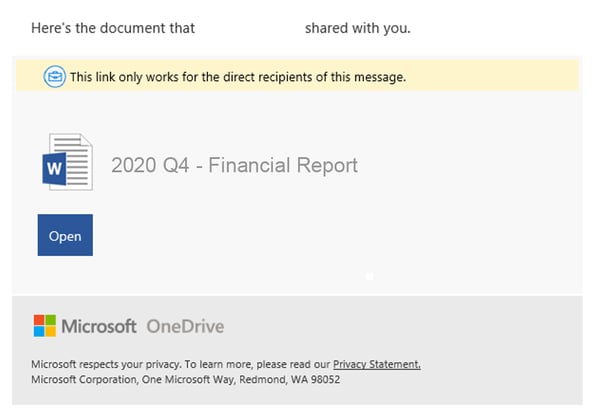
Phishing email example - OneDrive document shared
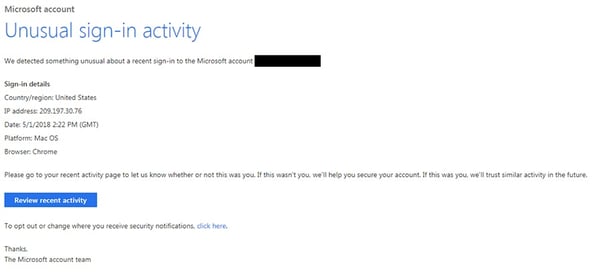
Phishing email example - notification of unusual sign-in activity
What the recipients of these emails don’t realise is when they click through the email and sign in, a copy of their credentials is sent back to the cyber-attacker.
But how much damage can phishing emails really do?
Sure, there might be some confidential information, but what monetary value is there in getting access to someone’s email?
While the contents of your accounts payable, CEO, HR or Office Manager’s email inbox may, at first thought, be inconsequential... After all, it’s not like they have direct access to your online business banking account, right?
Your CEO's or Office Manager's emails do have a perceived authority, which can be just as valuable, especially if it's taken advantage of. Take a minute to consider any one of the following three scenarios.
Oh, and yes, these actually happen.
Scenario A - Payroll New Bank Details
- A cyber-attacker sends a phishing email to your employee
- Your employee reads the phishing email and clicks a link to sign in
- The cyber-attacker receives a copy of your employees' credentials and logs into their email to send an email to your accounts/HR team requesting that their wages need to be paid into a new bank account.
- Your accounts/HR team updates the employees' bank details in your system and come payroll day, that team members wages get paid straight to the cyber-attacker.
Scenario B - Fake Invoice
- A cyber-attacker sends a personalised spear phishing email to your CEO
- Your CEO opens the compelling phishing email and clicks a link to sign in
- The cyber-attacker receives a copy of your CEO's credentials and logs into their email to send an email to your accounts payable team authorising the payment of an attached, fake invoice.
- Your Accounts payable team might reply to confirm the details with your CEO.
- The cyber-attacker intercepts the email and replies to confirm the request.
- The cyber-attacker deletes all records of the emails before your CEO notices what has happened.
Scenario C - Compromised Supplier
- A cyber-attacker sends a phishing email to one of your suppliers
- Your supplier opens the email and clicks a link to log in
- The cyber-attacker receives a copy of your suppliers' credentials and logs into their email to send an email to your accounts payable team notifying them that the suppliers' bank details have changed.
- Your accounts payable team update the bank details in your system
- The cyber-attacker sits back and waits for your supplier to send a genuine invoice
- Your accounts payable team settle the invoice having unknowingly transferred the money straight to the cyber attacker.
The sophistication of these cyber-attacks doesn’t stop there. Many modern phishing emails have been meticulously designed with harmless links in order to bypass your traditional security measures, before morphing into malicious content once they land in your inbox.
But there is light at the end of this story.
Friendly IT geeks got sophisticated too!
Defending your business against sophisticated attacks means you’ll need protection that’s even more sophisticated. Yes, an overly simplistic statement, but bear with me.
What if you could leverage the millions of dollars Microsoft spend on cyber security and use the live data from all of Microsoft’s touchpoints to detect cyber threats in real-time? Data, that only Microsoft can provide.
Think:
18,000,000,000 Bing web pages
400,000,000,000 Outlook emails
1,000,000,000 Windows devices
700,000,000 Azure accounts
450,000,000,000 monthly Microsoft authentications
Well, you can. And you don’t have to be a fortune 100 company to do so.
Enter: Microsoft 365 Business Premium
Microsoft 365 Business premium is a suite of advanced security tools, integrated collaboration apps (like MS Teams) and your trusty Office applications (think: Word, Excel, Outlook, etc..) all packaged together into a single monthly subscription tailored for businesses just like yours, with anywhere between 1 and 300 employees.
The Advanced Security and Management defences of Microsoft 365 Business Premium are built on something called the Intelligent Security Graph.
It’s a state-of-the-art security system that powers real time threat detection, response and remediation. And if you’re into massive amounts of data and technical jargon there’s an entire RAM-hungry-website devoted to it.
For those of you who want to keep things short and simple:
The Intelligent Security Graph gets updated anytime a new threat is detected anywhere on the planet. And with billions of Microsoft touch-points across the globe, this is arguably the single best source of cybersecurity data in the world.
So, how does this immense volume of data translate into security tools you can use to protect your business?
Office 365 Advanced Threat Protection
One of the security tools included in Microsoft 365 Business Premium is called Office 365 Advanced Threat Protection. Or just O365ATP for short. It just rolls off the tongue, right?
Fortunately, it does a much better job of stopping phishing attacks and cyber criminals from waltzing their way into your business like they own the place. Here’s how.
1. Safe Links
Most security software will scan the links in your emails to check if they redirect to a malicious website before they land in your inbox. That’s traditional stuff.
But, as we know, cyber-attackers got sophisticated. And they send sophisticated attacks. Like phishing emails that include harmless links to evade your security filters.
What’s sophisticated about that? You ask. Well, once that message bypasses your filters it changes those harmless links to something malicious. That’s scary stuff.
Every time you click on a link in an email, Safe Links will double check the destination of that link to make sure you’re not about to be sent somewhere you didn’t intend to go. Oh, and it also works with Microsoft Office documents too.
2. Safe Attachments
Very much like Safe Links, this opens every email attachment that you receive in a virtual environment and sits back to watch what happens next. If something out of the ordinary indicates that mischievous activity is about to run riot, that email won’t reach your inbox.
3. Anti-Phishing Intelligence
Look, we acknowledge that Microsoft loves a syllable, or eight, to name their cool stuff. And this is no exception.
Anti-Phishing Intelligence learns the way the users in your organisation communicate, so when a string of communications begins that are out of the ordinary, the system can gauge if one of the accounts has been compromised and is under the spell of a cyber-criminal.
There are more multi-syllabic security tools that Microsoft 365 Business Premium gives you too
1. Advanced-Multi Factor Authentication (MFA)
Yes, advanced multi-factor authentication (MFA) is also known as “that code you have to enter after your password”.
But please know that the ~12 seconds it takes for you to say it (and enter a code once every month or so), pales to the time and expense of dealing with a breach because you ‘didn’t want the inconvenience.'
For those of you that are fiercely opposed to this added layer of security, you’ll be happy to know that Advanced MFA gives you the option to bypass the MFA process when you’re logging in from trusted locations (such as your own office). Having said that, we strongly recommend that you just use it. All. The. Time.
Advanced MFA allows you to completely prohibit access from places where you don’t have any employees too. This helps protect your data from overseas attacks since you’ll know that those people logging on from <insert country of choice> are probably not part of your end-of-financial year retreat.
2. Microsoft Windows Defender
Windows Defender Antivirus is the next security component from this Advanced Threat Protection suite.
Without getting stuck into the technical jargon, this inclusive anti-virus product brings together a clever mix of machine learning, big-data and Microsoft cloud infrastructure (AKA the Intelligent Security Graph we spoke about earlier) to provide real-time protection against known, new and emerging threats.
3. Data Loss Prevention
From financial records and annual reports to secret recipes and your blueprints for intergalactic time travel, every business has information that they don’t want to have made public.
Data loss prevention helps you to automatically identify sensitive information across many locations (Think: Exchange, SharePoint, OneDrive, etc) and block access to that document or prevent that document from being shared outside of your organisation. Which is a welcome safety net for when mistakes happen.
4. Email and Document Encryption
When the time comes to legitimately share sensitive data outside of your organisation such as financial records to your accountant, for example. You can encrypt your email to ensure that only the intended recipient with the right credentials can open the email – even if it goes walkabout.
5. Device Management
I’m willing to guess that your business uses a variety of phones, tablets and laptops to access your data. I’m also willing to guess that you’re probably not keeping track of how these devices are being managed, secured and knowing how they’re moving from point to point.
Devices moving around with your office network isn’t a problem. It’s when they move cities, countries or become lost in environments that you can’t control that problems arise. Microsoft 365 Business premium includes a solution to manage your devices, even if they aren’t in your network.
It’s called Device Management, who would've guessed?
And while Microsoft isn’t in the running to win awards for their choice of names, their Device Management solution, that’s powered by Intune, has won the affection of many Fortune 100 companies.
So, whether you want to tightly manage devices owned by your company or lightly manage devices owned by your employees, Microsoft 365 Business Premium has you covered.
Enough about the bells and whistles, here’s the situation
If you’ve got this far, it’s likely that you currently have:
- A traditional cyber security solution in place,
- An understanding that you’re not getting as much protection or value from your current IT and security measures, and
- A bunch of ridiculously nice humans working in your organisation. Who poses a significant risk because they are:
- Human, and
- Ridiculously nice. So nice in fact, that they will go out of their way to help someone get whatever they need, even if that someone happens to be a deceitful IT geek.
Microsoft 365 Business Premium takes care of A and B, without costing the earth. In fact, it only costs $27.50 per user/month and it includes all of your apps from Office 365. This means, it replaces your current Office 365 subscription and you’ll be able to leverage all of the sophisticated security features to help protect your organisation against C.
Villains can be Heroes too
Given robots haven’t completely taken over our world just yet, humans aren’t going anywhere soon. But that doesn’t mean you have to roll the dice and hope that we are susceptible, albeit good-natured, creatures don’t do something dumb.
Despite Microsoft’s 365 Business Premium product stealing all the headlines (and syllables), your employees can actually be the heroes of this article.
Beyond arming your people with the right tools. Educating your team, so they can spot threats and protect your business is the single best thing you can do. Making the effort to show them the latest trends, how to avoid ransomware and the importance of exercising caution (and common sense) is an excellent investment that will, over time, build an organisational culture where your personal and business security is paramount.
It’s easier than it might seem. And with the right IT Partner (and their cyber security insights and awareness material) they can help you do it.
Get modern. Get secure. And get more value with the right IT Partner
Thanks to some seriously clever cloud technology (and the millions of dollars that Microsoft spends on research and development. Every. Single. Year.) modernising your IT and your security with a sophisticated cyber-defence is no longer just for the big girls (and boys) in town.
Add this to your IT partner's inclusive vCIO services, support and cyber security expertise and your business will have the sophistication of products like Microsoft 365 Business Premium and the insights from IT experts to get more value from your IT for a transparent all-inclusive fixed monthly cost. This means “making do” and rolling the dice with your traditional security measures is no longer your only strategic or affordable option.