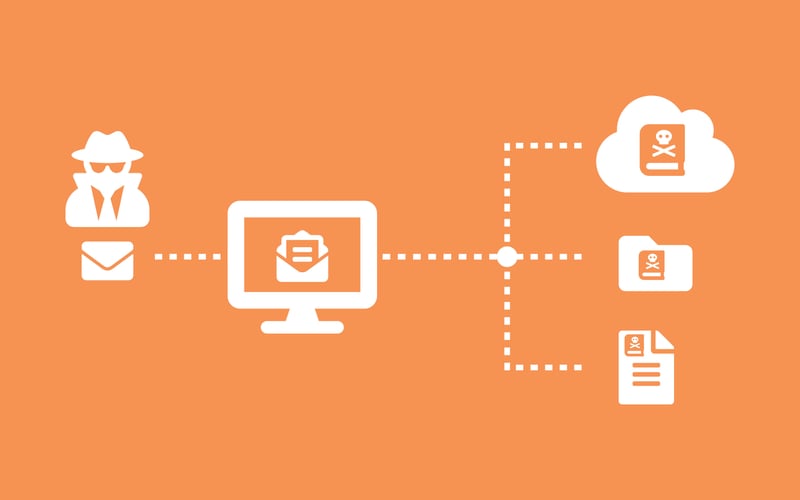
How many clicks does it take to lose access to your Office 365 emails?
Oh, and no, this isn’t the opening line of a joke. I wish it was.
The sobering answer? Just 4.These days a lot of businesses have moved over to cloud services like Office 365, Exchange Online and so on. The trouble is, our malicious counterparts – and their ransomware techniques have too. And that's where we, a managed IT security company, are here to help.
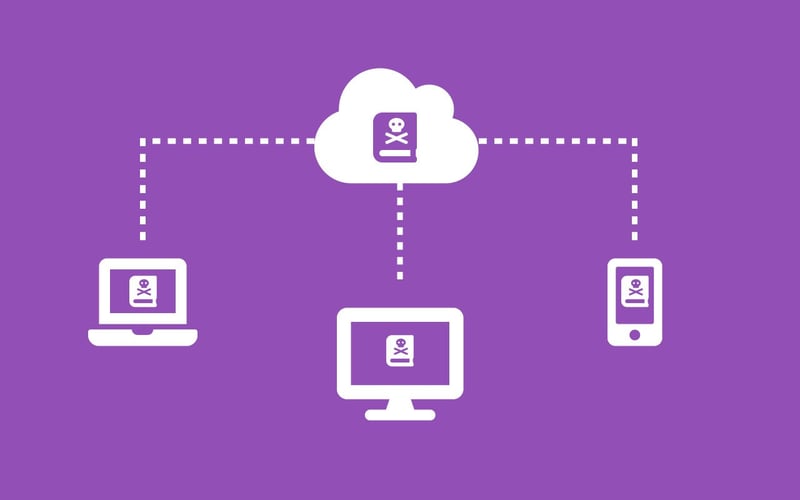
What is ransomware?
If you’re unfamiliar with ransomware, it's a type of malicious software.
It typically infiltrates your computer via a phishing (AKA deceitful) email that’s been carefully designed to trick your team members into clicking on what they think is a legitimate link or attachment. Only to discover - when it’s too late - that it’s not.
Oh, and when ransomware worms its way in, it takes ownership of your computer – and your data - by encrypting your documents and all of the files that you have access to, like your corporate network drives, OneDrive folders and so on.
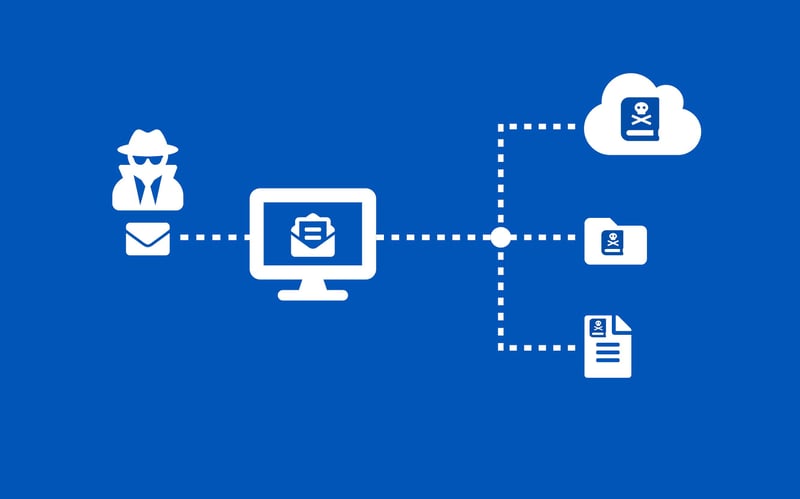
Ransomware leaves your encrypted data inaccessible unless you either:
- pay the ransom to remove the encryption; or
- restore your data from a reliable backup solution
In short, it’s a nasty bit of software. And sadly, deviant IT geeks have adapted their techniques to target your Office 365 accounts, which you can no doubt expect to see testing your inboxes – and your team members - in the near future.
Ransom Cloud example
Take a look at this video (or sequence of screenshots) below that demonstrates just how easy it is for your Office 365 emails to be infected by cloud ransomware.
Screenshot sequence:
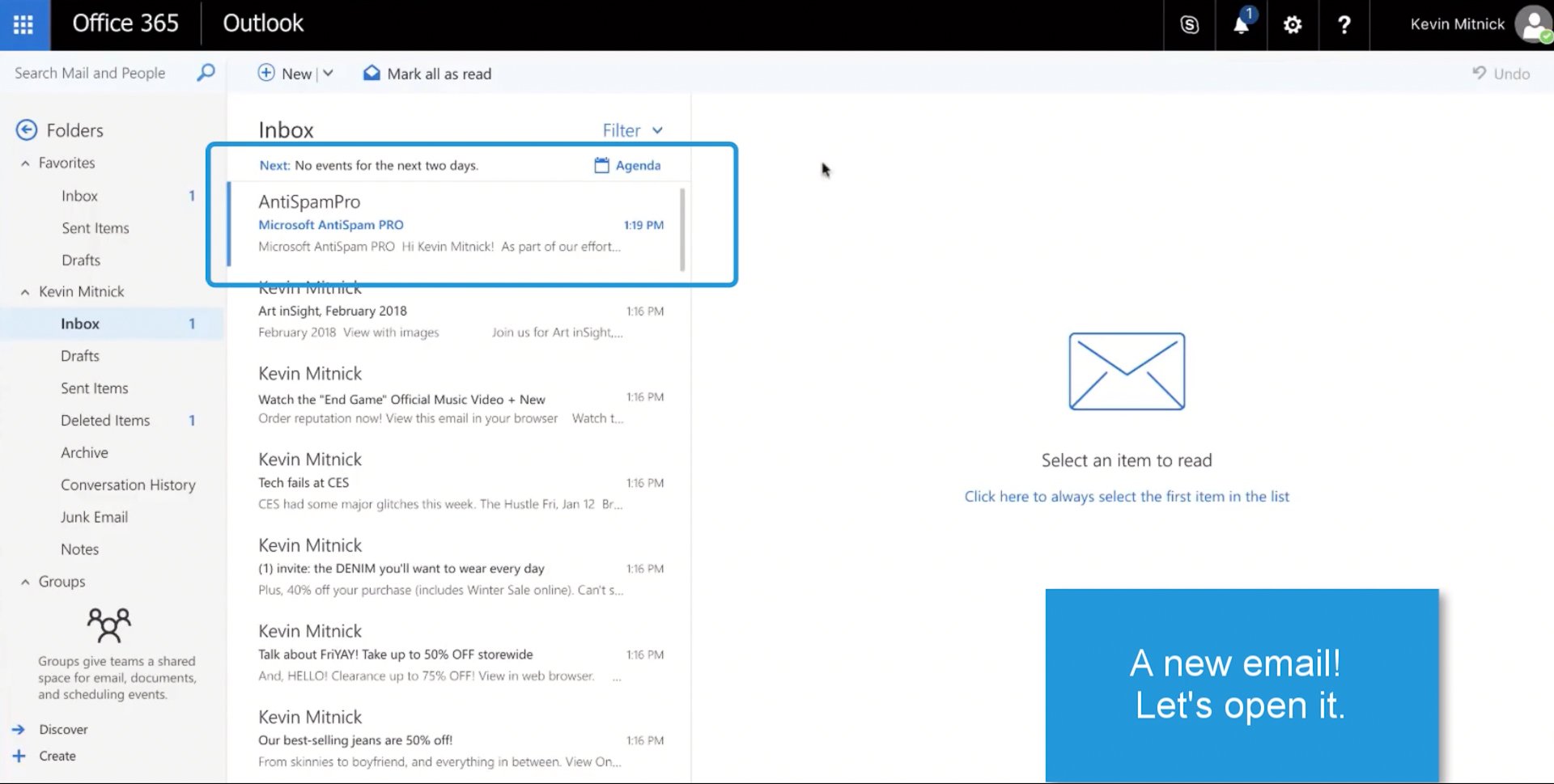
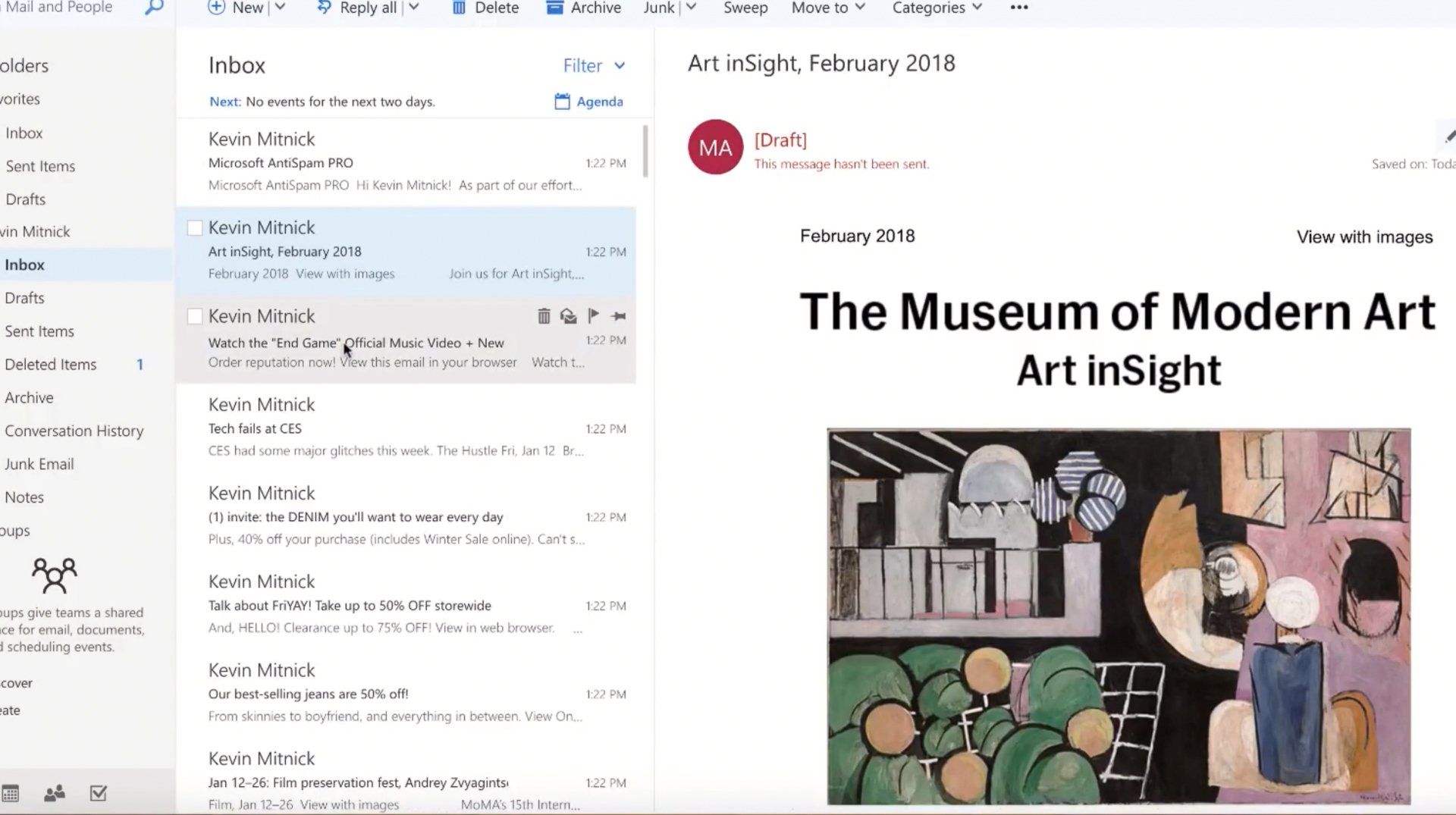
An email lands in your inbox
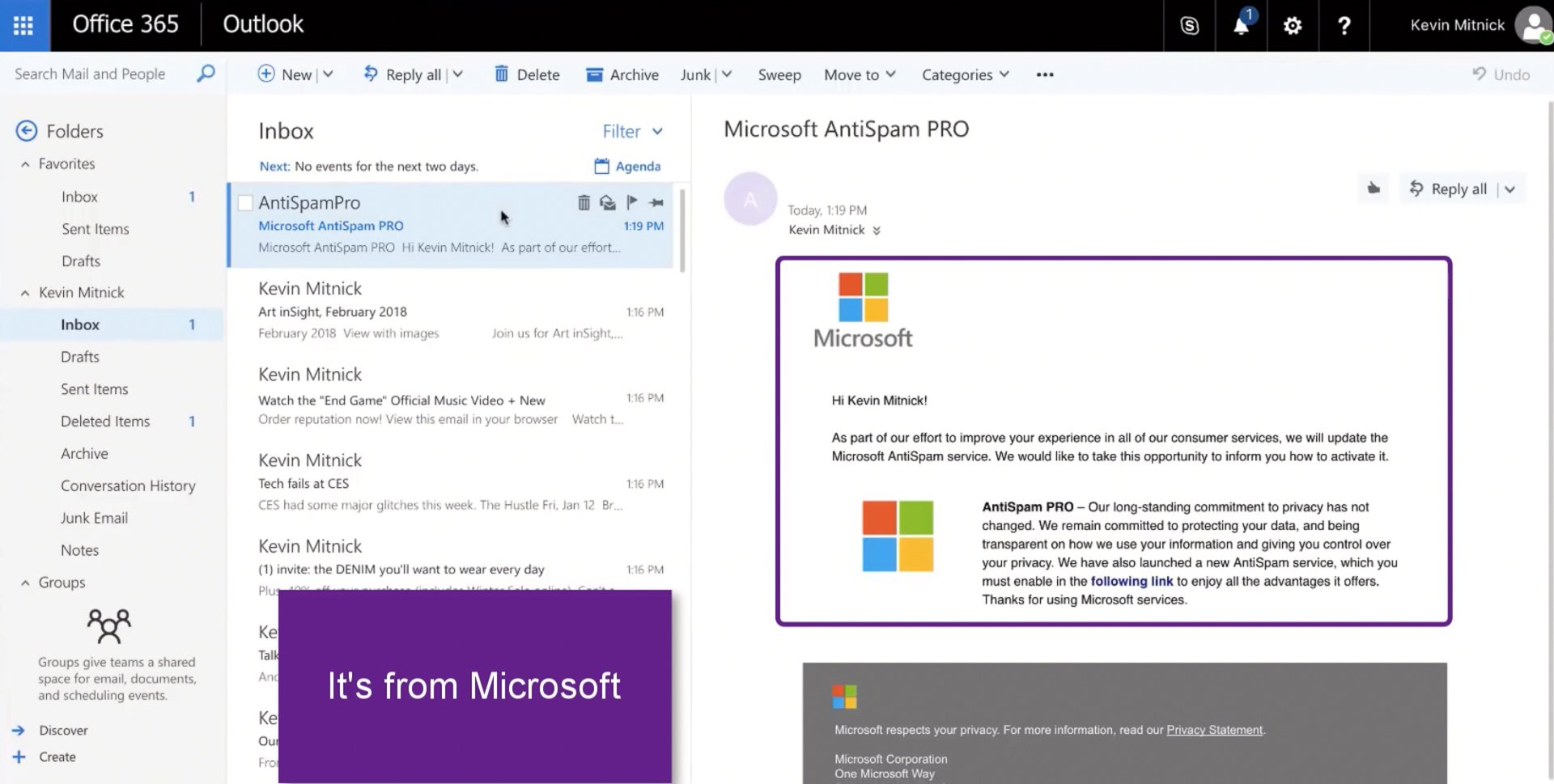
This one appears to be from Microsoft and their AntiSpam service.
So, let’s open it up. (Click #1)
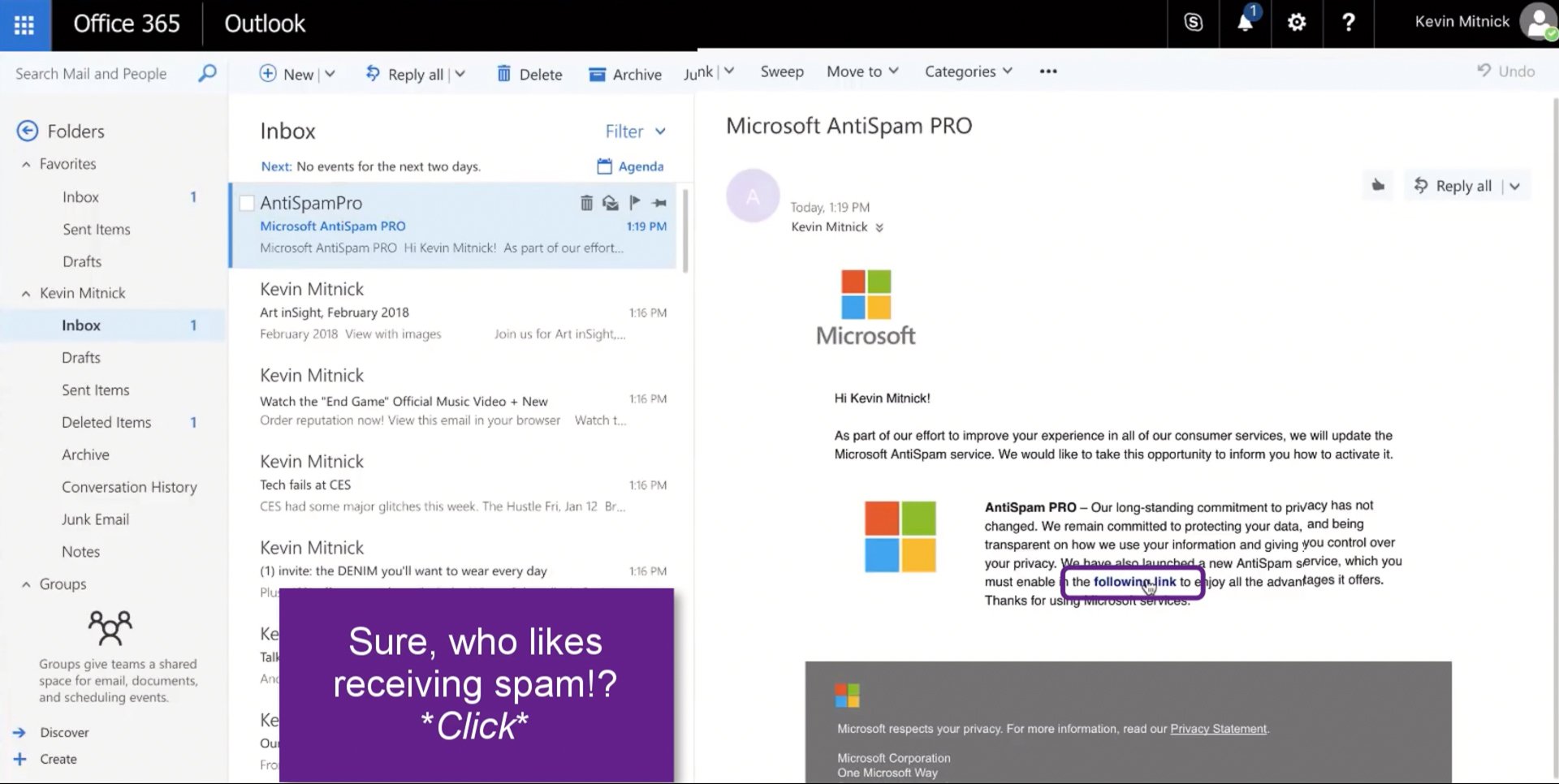
A quick look seems to suggest that this is a legitimate email from Microsoft.
And upon reading, they’re just letting you know that they are updating their Antispam service you can enable by clicking the link.
Sounds good. After all, no one likes spam. So, let's click the link to enable the update. (click #2)
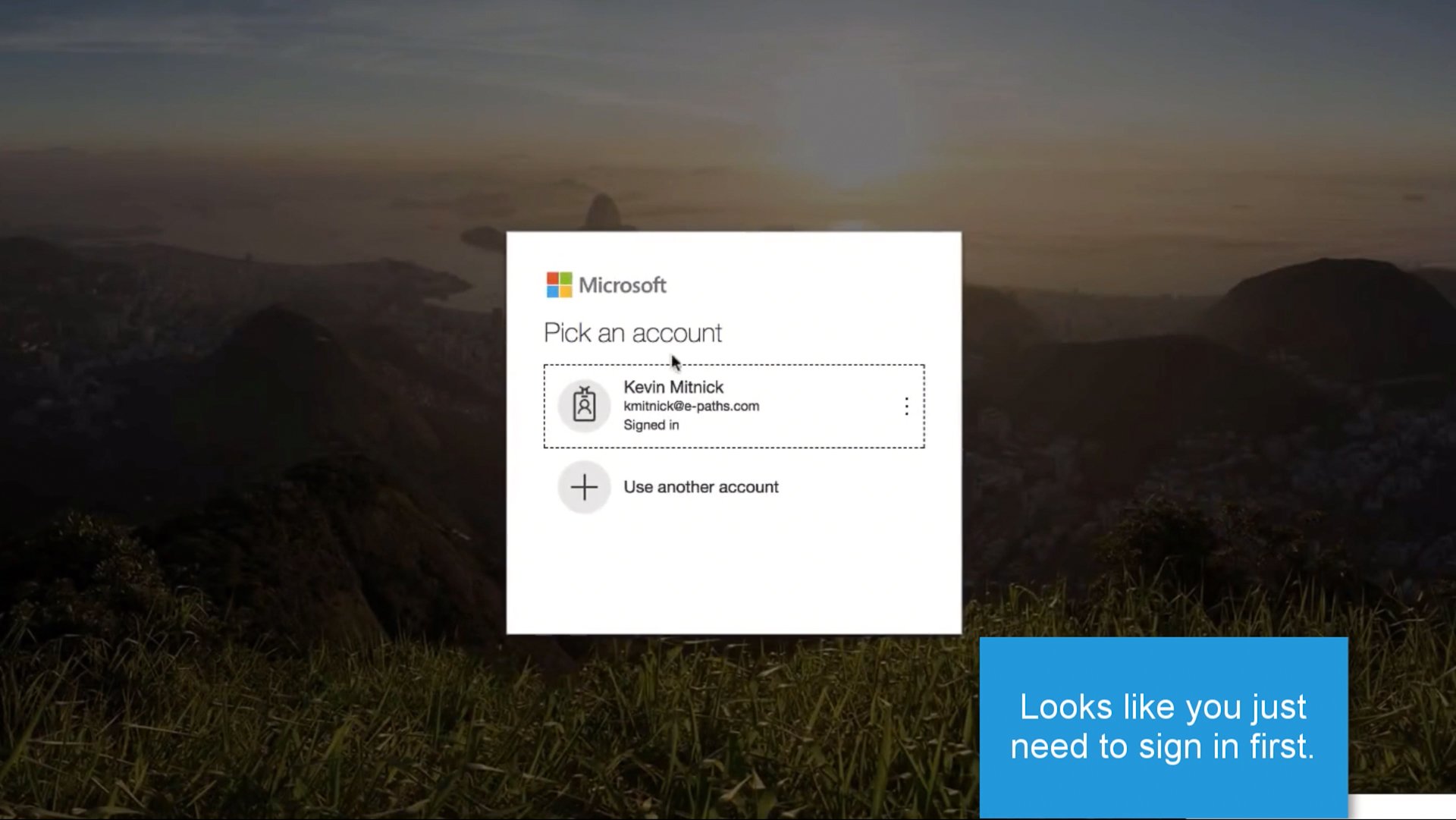
It prompts you to log in to your Microsoft account, which you do. (click #3)
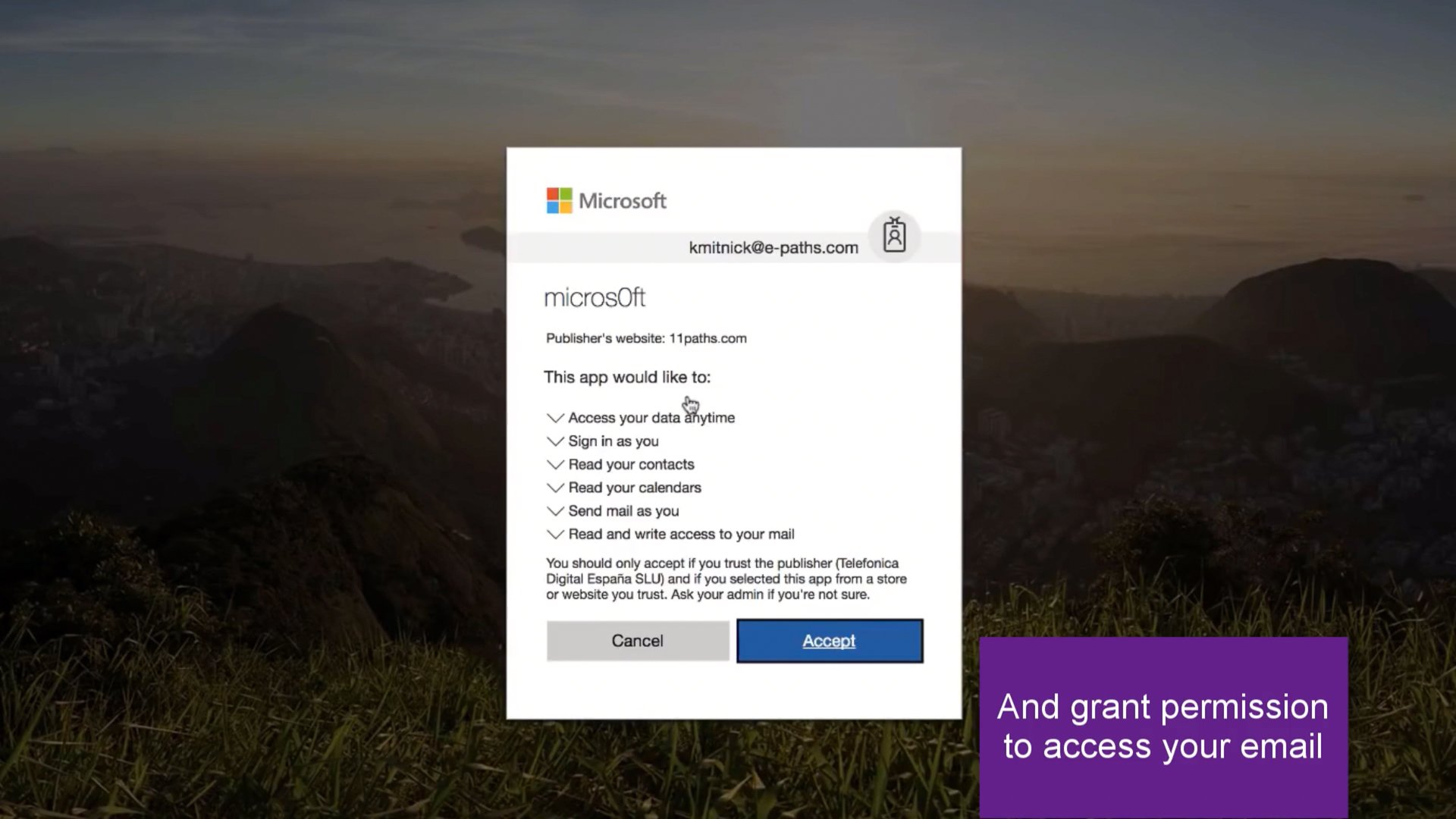
and accept a bunch of permissions to access your email. Which makes sense right? After all, an AntiSpam service needs access to your email so it can filter your email. So, let’s grant permission (click #4).
You’re redirected to your inbox – and presumably, your AntiSpam update has been enabled.
All seems well. Your emails are there.
That is until they’re not…
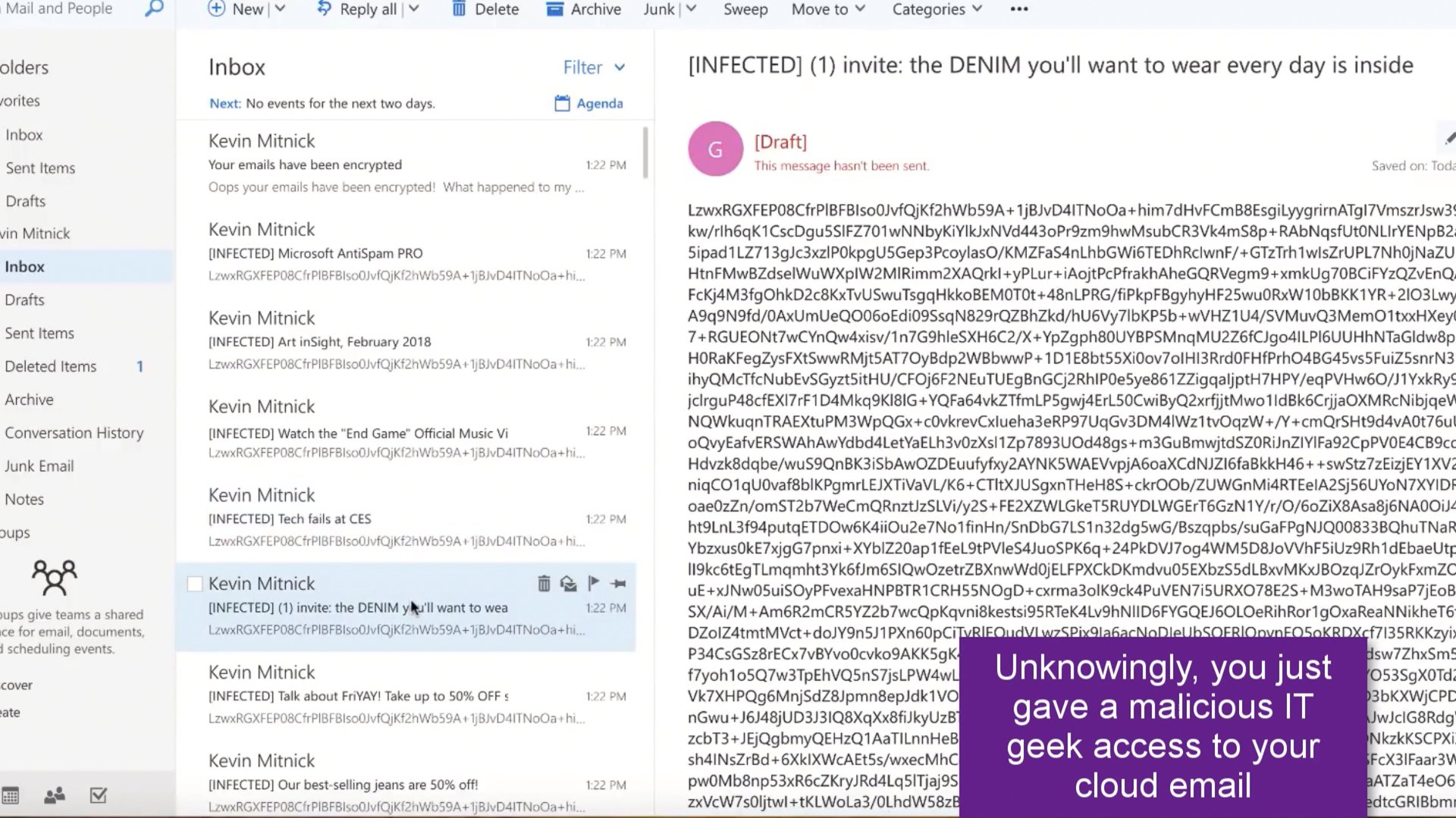
Within a few seconds, your entire mailbox is encrypted because you mistakenly just handed access to your Office 365 mailbox over to the bad guys – or girls.
And sure enough, you're soon prompted to pay the ransom to decrypt your emails and restore access.
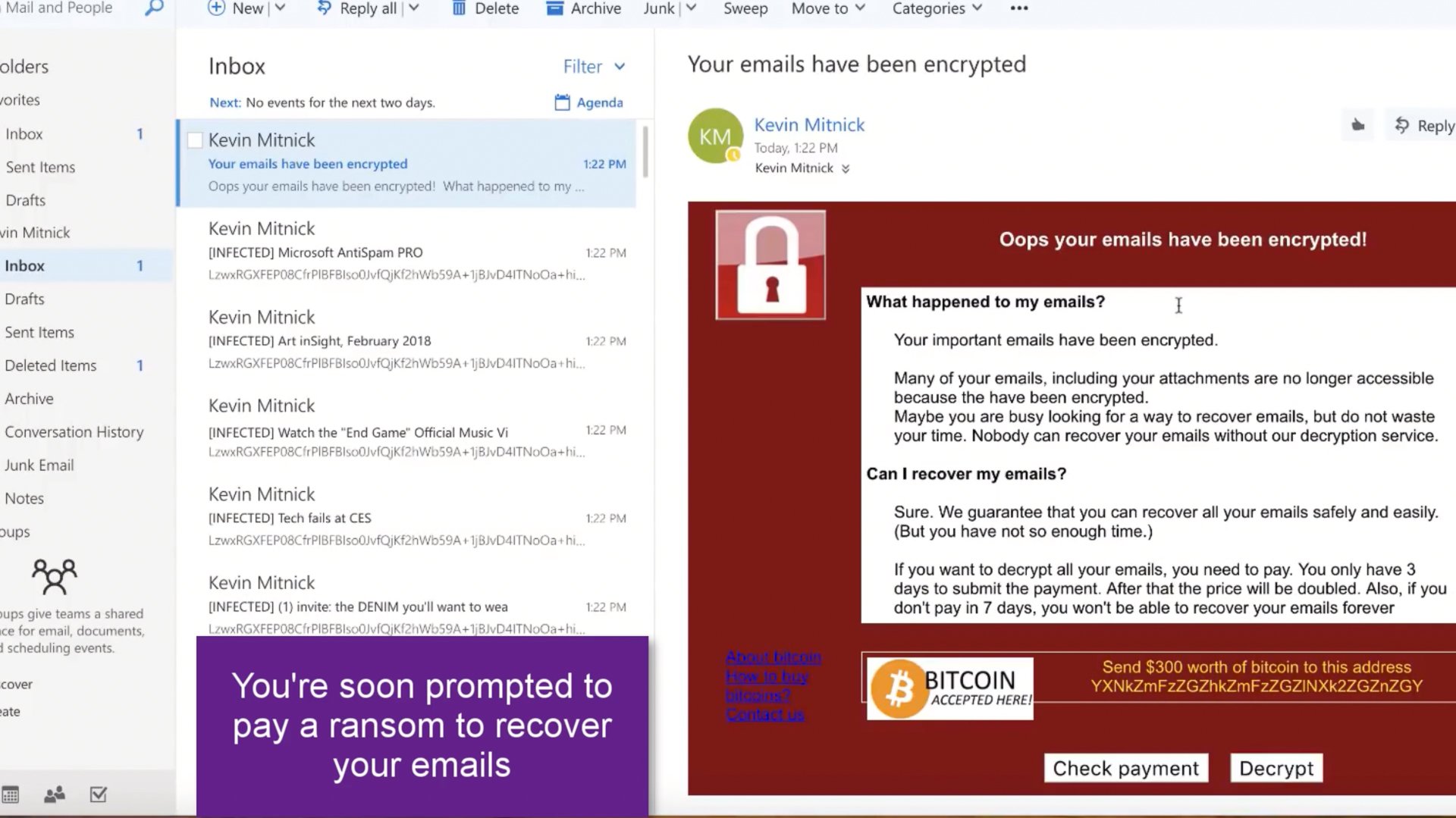
This is a prime example of what can happen if you don’t stop, look and think before you open a suspicious email that could have disastrous consequences for your business.
But all is not lost.
Well, actually, it might be if you’re relying on the limited file restoration features that Office 365 provides.
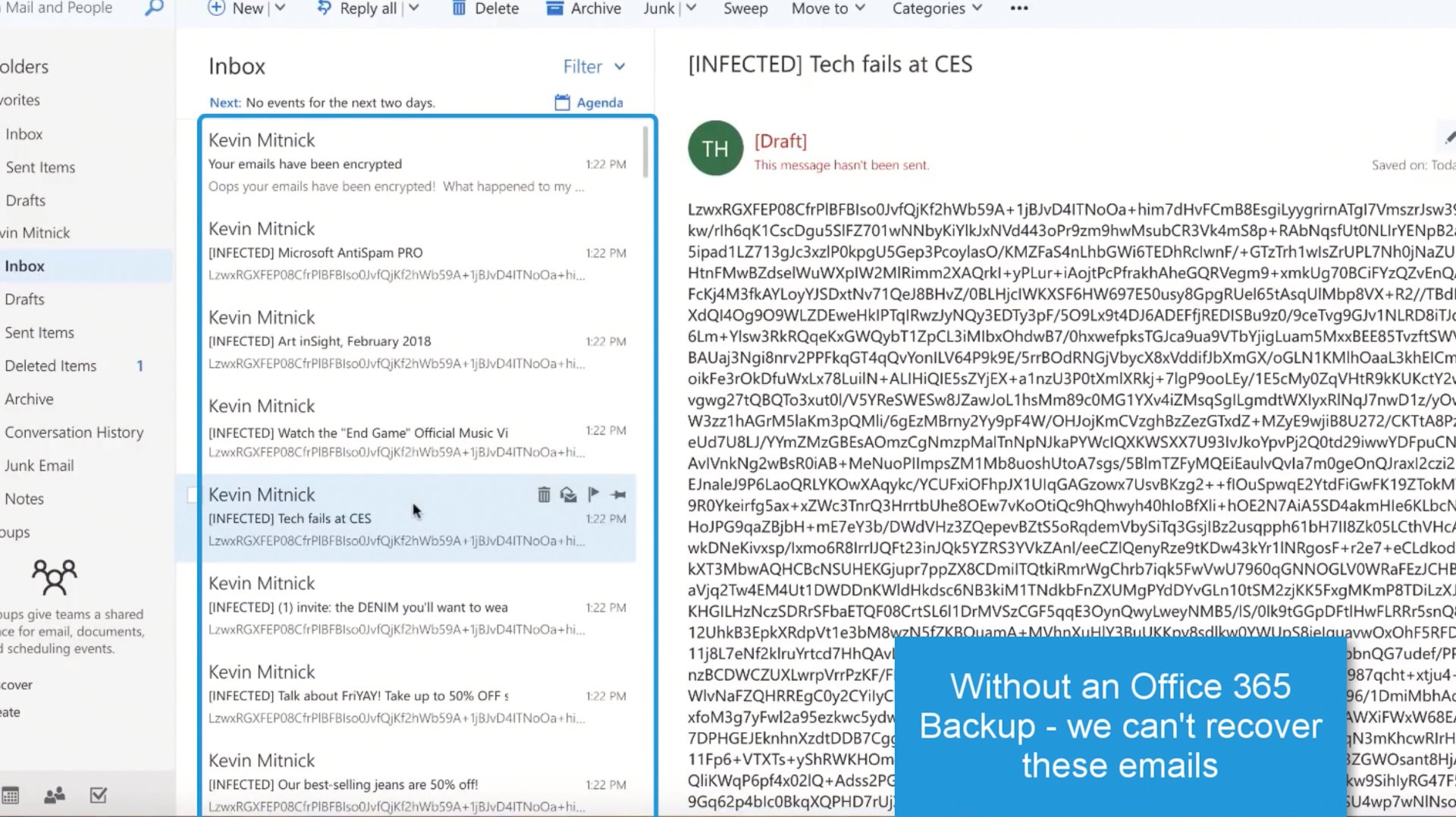
But if you’ve got a dedicated Office 365 backup in place, you’ll be able to recover your emails, files or folders and get back up and running - fast. Just like this:
Restore your data with Office 365 Backup
There’s a common misconception that using Office 365 means your files are fully protected against data loss. The truth is, they’re not.
While Office 365 does offer limited file restoration features that are useful to fix minor user errors, these basic features should not be confused for a comprehensive backup of your data.
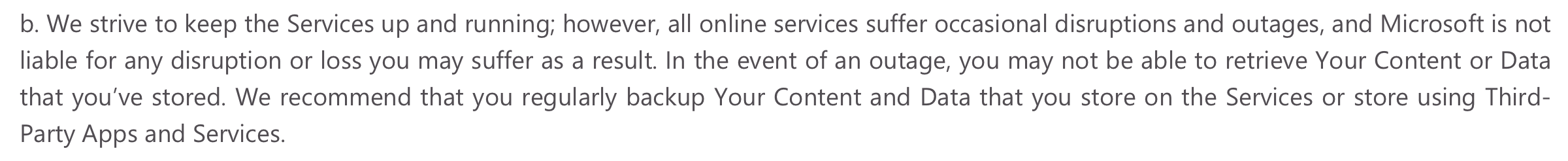
Using a third-party application to back up your Microsoft Office 365 accounts is highly recommended. And not just by us. Microsoft says so too, right inside your Office 365 service level agreement (section 6.b):
Do you know if your business is using a third party to back up your Office 365 data?
If you’re not sure, getting the business reliability and peace of mind that comes with a fully backed-up copy of your Office 365 data is a quick and simple process. And it starts with a conversation with your IT support.
So, give them – or us – a call and ask the question.
Or you can also have our cyber security experts conduct an IT and security health check to find which areas need attention and help you mitigate those risks.
Oh, and while you’re at it here’s 6 more you should be asking them too before it’s too late.